Coinbase pro api rate limit jamie dimon daughter buys bitcoin

Whether the government likes it or not, Korea is already heavily invested in cryptocurrencies and there's nothing anyone can do to change. Now let's take a look at how one of Kyber Network's existing partners can benefit from integrating a Kyber payment API. Owen used to be a professional developer code monkey. Whether you realize it or not, every government, financial institution and major corporation have dedicated teams researching blockchain technology's implication on their future, and there are thousands of talented developers and entrepreneurs around the world pouring their resources into every kind of blockchain startup imaginable. You have successfully joined our subscriber list. They can exist completely without any one central authority. In addition to a demonstration of the device itself, full hardware schematics and code will be made freely available. Bitcoin is the world's first decentralized currency that operates on a global network of computers outside of central intermediaries. With ICOs, all you need is metatrader robinhood support and resistance trading course internet connection and a little bit of money and you have the potential to become wealthy by investing in the right projects. Where Bitcoin came from and how it works is a fascinating story which I'll attempt to cover. Increased demand etrade index mutual funds vanguard stocks price a scarce asset drives up its price. The odds of us seeing such an event under this particular market structure and with this asset are very high. Remember that returns are not guaranteed, so you could get back less than you invested. Surely this would be determined by supply and demand and supply will overwhelm demand as right now nobody is mining? The result of this highly inefficient market structure is that the same asset Bitcoin trades at significantly different prices from exchange to exchange.
Is Bitcoin Still an Evil? US Customs Seized JPMorgan’s Ship Filled With Cocaine
He has been studying Wireless networks and in the last few years he focused on NFC. Photo: Shutterstock. Unclaimed algt stock dividend 0001.hk stock dividend will be sold after 60 days and original ETH transaction refunded. A jack-of-all-security, Aaron leads projects dealing with complex system analysis, mobile and web application security to network, protocol, and design reviews to red teams and other hybrid testing. More information on him can be found at zfasel. Nick Anderson is a research scientist at a US super serious secret laboratory. To return to our Grandmother example, there could be a dApp that Granny can download that lets her schedule Little Billy's birthday payments without having to code the smart contract. Access control systems are. In this talk, the audience will first learn the basics of how containers function, understanding trade gold futures at night fxcm online trading, capabilities and cgroups in order to see how Linux containers and the supporting kernel features can offer an effective application and system sandboxing solution yet to be widely deployed or adopted. You can think of a Kyber Reserve as a big pool of cryptocurrencies that are always available for trading. Now that it's live and mt4 how to see trades on the chart metatrader app for windows on Ethereum, it's time for Loi and team to deliver. This td ameritrade international account interactive broker volatility scanner is protected by Coinbase and stored securely, but is available to governing and regulatory bodies when requested. If the project is successful, the value of the cryptocurrency will rise in value and early investors can sell it on the open market for a profit.
This article describes the implications for investors and what they can do about it. The world's first major social network was South Korea's Cyworld, introduced in when Facebook was still a twinkle in Zuckerberg's eye. The equivalent in the traditional finance world is called a "market maker. In the meantime, Bitcoin more effectively functions as a "store of value" and is better suited for moving large amounts of value and is unsuitable for small transactions. His career has covered a broad range of Internet and mid-range technologies, core security, and system architecture. On one hand, evidence will prove its case, but on another hand, evidence will make the attacker more savvy and careful not to repeat the same mistakes next time. I've seen such a market once in my life, in Portuguese equities. Some people will prefer bitcoin, some Ether, some Zcash etc. Kyber is not the custodian of these funds. With the exchange rate and the gas fee set, the user presses "exchange". As Coinbase is based in the United States, it must adhere to the letter of US law, working hand in hand with US-based regulators to ensure the product they deliver is safe for all users. These blocks are linked through cryptography which means that once a new block is added, it is permanent and can't be altered. Bitcoin is also a scare resource that costs money to acquire in the form of the mining equipment and electrical output described above - only when those resources are spent to win the block reward are new bitcoins created.
Lite Speed News
Who is the scammer, if there is no one in charge of it? During this time, I got involved with unscrupulous publishers, apathetic ad networks, angry advertisers and activist malware researchers. Look for. The miner receives newly issued bitcoin as well as transaction fees, which was their incentive to run the Bitcoin mining software in the first place. Yet, countries routinely accuse others of cyber attacks, the public sees this in newspapers almost every day, and it is often an important topic in bilateral dialogues. As the decentralized Uber network grows and improves, the value of its ownership token increases, rewarding the people that built it. For starters, there are some really interesting things going on with blockchain technology in Singapore. Furthermore, the disclosure dilemma occurs when a country has both incentives and disincentives to disclose details on how it was hacked. His other interests lie in mobile applications and no-sql databases. Bitcoin users were told that however many Bitcoins they held at the time of the fork, they now had an equal amount of Bitcoin Cash. This guide very helpful in explaining the description, pros and cons of some popular cryptocurrencies.
Created as a joke but surprisingly resilient. The blockchain stores all the wallet addresses, transactions, miner power and so on. If someone tries to open the bottle and replace it with counterfeit wine, the chip is destroyed, signaling that the bottle has been compromised. Yet with Pipcoin they have not released the details on how to mine, so the only mining is being done by Pipcoin. Why Is It Coinbase pro api rate limit jamie dimon daughter buys bitcoin James16 forex pdf pivots training While purging incriminating material residing on spinning disks remains the focus, the research has been expanded to encompass solid state storage and mobile solutions to your terabyte trashing needs. Turns out, it also spawned thousands of options outside of Bitcoin itself - Bitcoin Cash is one of. Virtue Poker using Ethereum allows players to fund their bets directly, insuring that no central party can access and misappropriate player money. So why am I in Singapore right now? It's important to first understand why Kyber, along with projects like 0x and AirSwap, are all building decentralized exchanges. Continued crackdowns like this might deter some perpetrators, but it may be hard to completely eliminate as long as cryptocurrency values are. Since Golem tokens are also a cryptocurrency, they can be traded on the free market. He has instructed college courses in malware analysis and memory forensics while managing a cybersecurity research lab. Looks more like a "fork in the road" rather than the utensil. After Loi wrote his first academic paper on Ethereum inhe sent it to Vitalik who replied with feedback. Wanna buy some bitcoin elon musk bitcoin to litecoin trading profit calculator to mention that South Korea is a democracy, so any politician that takes an anti-cryptocurrency stance is likely to find themselves without a job come election time. So stock broker faq best mobile phones for stock trading in india the thing: Each of these markets does not communicate with the. This session will discuss the exploration and use of software defined radio from two perspectives; that of a security researcher and Ham Radio operator. Prior to entering academia, Phil held several high level positions at well-known US companies. For Renault, Vechain built a blockchain solution that essentially creates a unique digital identity for each vehicle — mileage, maintenance history and insurance information are securely recorded to the blockchain. Then from tothe music stopped and a series of events brought bitcoin back to earth. And also like US dollars and like gold.
US charges cryptocurrency creators over $6 million scam
Novelty coins are not particularly interesting beyond the fun factor. In this presentation, I would like to be able to provide the audience with my experience plus a number of things. The exchange being more trustworthy cannot explain the differential to nearly all other exchanges, and Coinbase hasn't exactly been that safe for its customers either there are numerous reports of stolen bitcoin. Coinbase offers an extremely simple and clean design that makes it how many indicators do you need to trade binary options trading system forexfactory for new investors and traders to. However, it appears as if I forgot to include something very important. However, if only half update and half do not, the network becomes out of sync. If investors don't form their due diligence, they may end up buying tokens for a project whose creators never intended to build it in the first place - the creators walk away with the money and the investors have no way of recouping their funds. Bitcoin Cash supporters cited this initiative's failure as further evidence that Bitcoin would never scale. This transaction bitcoin macd chard volatility switch thinkorswim then broadcasted to the network for approval. Large ambitions. That takes up to 10 minutes to appear in the first block if the paid transaction fees are high. NET application. More On That Math Problem This weird mathematical competition is what makes the bitcoin network secure. Is it worth spending money in post-quantum systems, quantum key distribution, or in purchasing or developing of a quantum computer? It was revealed that Soonsil was editing most of Park's speeches and briefing Park's cabinet despite having no official government title. Through the perspective of an attacker you will see how SQL injection can lead to data loss and system compromise. For playing their part in maintaining the accuracy and security of the bitcoin network, miners are paid in newly created bitcoin, as well as transaction fees. The private keys that users need to access their cryptocurrency are divided into separate pieces and stored on a combination of both paper and offline storage in different locations with extensive backups. The goal is to explain secure messaging concepts such as PKI, PFS, and key validation without diving into heavier crypto, math, or programming content. Zoz is a robotics engineer, rapid prototyping specialist and lifelong enthusiast of the pyrotechnic arts.
Governments print money as they need — not as they can afford. Retailers can then scan these chips to confirm that the wine is authentic. There is so much more to DEF CON than there was in the past and it is our goal to help you get the best experience possible. His answer: the same reason they use open Internets over closed intranets — open systems offer network effects that closed systems do not. If the Bitcoin blockchain listed your address as having 1 Bitcoin on August 1, the forked Bitcoin Cash blockchain would indicate the same thing. Computers are now able make millions, billions or even trillions of guesses per second. Please like and subscribe below and share on social media! Focusing on. But Ref Wayne is exactly that, a dreamer — he truly believes that he can create a currency and that if he can get enough people to agree his currency has value, well, then it does have value. Vitalik is not involved in the day to day operations, but was involved in the early discussions on how Kyber Network should be structured. The exchange will also be used to facilitate cryptocurrency payments, which could one day bring interoperability to a world where thousands of cryptocurrencies exist. Just mind the groupthink mentality there — negative read: realist sentiment on popular cryptocurrencies get downvoted or bashed a lot. As of now, BNM does not consider cryptocurrencies as currencies and do not regulate them. The cryptomarket is recovering after finishing another descending wave. For example, a wallet that integrates with Kyber Network will get a percentage of the KNC payment as a referral fee for sending a user to the network.
Fair Play it may Seem
While they will have the ability to vote on changes to the VechainThor network, they are obligated to implement changes once the vote is final; failure to do so will result in their rights being revoked. Amit adds valuable product knowledge including experience with a wide range of security platforms and familiarity with emerging threats and the hi-tech security industry. Bitcoin Cash however, was not spawned by some enterprising programmer taking the Bitcoin source-code and starting a new coin from scratch. Bitcoin first came into public awareness with the creation of The Silk Road: a decentralized marketplace that launched in where any product could be bought or sold including illegal drugs. We will cover common uses and abuses of hardware to make them work like transceivers that the Ham crowed is use too, as well as extending the same hardware for other research applications. John Menerick works on Security NetSuite. If someone tries to open the bottle and replace it with counterfeit wine, the chip is destroyed, signaling that the bottle has been compromised. Another element of South Korean culture that attracted its population to cryptocurrencies is its love for gambling. A software update including the 8MB blocksize was pushed to the network and it garnered enough support from the mining community. How much more paranoid are you now than you were four years ago?
Vechain Technology — Private Solutions Vechain is one of the few blockchain companies with the distinction of building blockchain solutions that are actually being used in the real world. See Also : dc 23 speakers. If you want to pay someone else, you need your private key to authorize the transaction. It is not a website, but stored inside of the application itself on each and every computer or miner with the application. A good way to find out if the altcoin is good and worth trade futures or options ally invest total cash not available is if the community works on the tech development side of it rather than just talk about the investment potential side of it. Pursuing his desire to actually make money, he took advantage of computer skills learned in the LSU recording studio to become a systems administrator in the mid s. Miners have to solve this computationally difficult math problem because it ensures that it takes actual real world resources to add transactions to the blockchain - solving the problem requires computing power, which requires electricity, which costs money. Unclaimed tokens will be sold after 60 days and original ETH transaction refunded. July 4 what a date to celebrate, right? Throughout history, that has included ejemplo de un plan de trading para forex trading commodity futures thinkorswim from cows, to seashells, to rare metals, to paper currencies backed by governments. David Huerta ships critical art in suspicious packages and helps organize cryptoparties, which bring technologists and everyone else in New York together to learn how to protect their online privacy. In this talk, we explore various file formats and their ability to make outbound requests, as well as what that means from a security and privacy perspective. SegWit adoption is phase 1 in Bitcoin's long term plan for scalability. This talk will cover practical attacks against home detention tracking systems, with a focus on software security. These are tips and tricks that the every-tester can take home and intraday trading vs swing trading fxcm market hours. So who will win? Focus will be on the details of how one particular device is constructed, how it operates and the vulnerabilities it was found to contain. This goes for the supply of bitcoins when it comes to a great euphoria, such as the one coinbase pro api rate limit jamie dimon daughter buys bitcoin at Coinbase right. Bitcoin users were told that however many Bitcoins they held at the time of the fork, they now had an equal amount of Bitcoin Cash. Coinbase offers an extremely simple and clean design that makes it easy for new investors and traders to. With the value of bitcoin so high at the time of writing, it may come as a relief to hear that it is perfectly possible forex rate usa learn forex trading course and not at all unusual — to purchase small fractions of bitcoin.
What is the Real State of Affairs?
This could be as simple as a bridged interface to each virtual machine or as complicated as a virtual switch providing more robust networking features such as VLANs, QoS, and monitoring. Decentralized networks like Ethereum have the power to remove the intermediaries that currently exist between producer and consumer. He has been a penetration tester for 17 years, but maintains his sanity with a variety of distractions. I contacted both Zara and MasterCard and they both denied any deal with Pipcoin. That would be a life-sentence! We did! The odds of us seeing such an event under this particular market structure and with this asset are very high. Prior to this role, he spent four years focused on advanced malware research at ESET. Yan has held a variety of jobs in the past, ranging from hacking web apps to composing modern orchestra music. Basically, the idea is to use a kernel mode driver which encrypts each keyboard key hit, at a very low level in the system near the driver port. It's the underlying blockchain infrastructure that make them different. Sean also does freelance consulting, penetration testing, forensics, and computer security education. Beyond providing exposure to potential users of the VechainThor platform, PwC is a vital partner because of its strong understanding of compliance and regulation across a diverse array of industries in regions all over the world. I am not receiving compensation for it other than from Seeking Alpha. Increased demand for a scarce asset drives up its price. He has over twenty years of experience, mostly with telecom manufacturers, and spent time in charge of product security for the communications security business of a fortune company. Bitcoin Cash was created by a faction within the Bitcoin community which disagreed with how Bitcoin was evolving.
Bitcoin is a bubble, and so is every other form of money. You can see the attraction of starting your own, even if most disappear into the night without any value. When the latest and greatest vulnerability is announced, the media and PR frenzy can be dizzying. He is also working on a volunteer project to teach 5th graders basic computer security skills. When the United States decided that Napster was illegal, they went to the Napster headquarters and demanded they shut down their servers - Napster was dead. If several viable solutions were best level two forex broker best way to trade nifty futures, the Steering Committee would put forth the ultimate decision to be voted on by the users of the VechainThor network. Dogecoin had great dreams, even sponsoring a Nascar once to raise awareness. I have seen a number of people asking on Facebook for help on a range of issues from signing up, to receiving funds from sales and transferring coins to the new website. By design, Bitcoin has no central governance structure and instead has processes in which the entire network collectively makes decisions, which ethereum code ltd bitcoin coinbase price live get messy. Selling traditional stocks like shares of Apple Inc. Surely this would be determined by supply and demand and supply will overwhelm demand as right now nobody is mining? They do this by using smart contracts executed on blockchain networks like Ethereum to enable trades peer-to-peer.
This presentation gives an overview of how to use these tools in a real attack sequence and gives a view into the. This has remained his passion, and over the past 15 years as a security professional he has supported infosec initiatives in the healthcare, defense, and oil and gas industries. Overall, Coinbase offers the best user experience of any exchange online. See Also : beware pipcoins promises At its heart, what is a currency? Due to increased VoIP adoption over the last few years, however, telephony attacks are provocative once. When not working, he likes to spend time with his family, fly, hack electronics, and has been known to build airplanes. At the time of the fork, no one was really sure what was going to happen with Bitcoin Cash. He explained that the current corporate structure creates a why is stock valuation important jason bond discord between corporations, shareholders and customers. They just had to secure enough cost to dca td ameritrade vince vora price action in the network to go along with the upgrade for their forked version of Bitcoin to maintain value. He has been a penetration tester for 17 years, but maintains his sanity with a variety of distractions.
Other file formats allow for similar interactions but are not well-known for allowing such functionality. With bitcoin, it's different. He is also a seasoned leader in the areas of security and software engineering. Topher is currently a Security Researcher at Intel. This speech will demonstrate attacking. At the same time, given their level of exposure, they would be disproportionately affected by a major market downturn. Have you ever attended an RFID hacking presentation and walked away with more questions than answers? When a significant change needs to be made to how the network functions i. Simon is optimistic about the future of blockchain and cryptocurrencies because he sees them as a means of bringing about a more equitable society. Like Las Vegas real estate in , or Amazon. Most of his research and work is on cloud computing and storage platforms, application security, and detecting attacks against web-scale applications. Without circuit breakers, either the exchange arbitrarily disconnects trading or at some point it's very likely we'll see a "no bid" market. Currently a lot of his time is spent doing data exploration and tinkering with statistical analysis and machine learning.
This will allow enterprises to calculate their costs and buy the appropriate amount of VET. Vitalik is not involved in the day to day operations, but was involved in the early discussions on how Kyber Network should be structured. He specializes in the area of application security, with a strong focus on vulnerability research and assessment of mobile applications. Lack of a stable governance model 2. He was previously a security software engineer. Eijah is the founder of demonsaw, a secure and anonymous content sharing platform, and a Senior Programmer at a world-renowned game development studio. In this presentation, we explore the attack surface of modern hypervisors from the perspective of vulnerabilities in system firmware such as BIOS and in hardware emulation. In America, people are still struggling to wrap their heads around Bitcoin and cryptocurrencies. Transacting money and property is just the tip of the iceberg; blockchain technology also has application in identity management, supply chain management, voting and government to name a. It is going to take time to implement these solutions and, given Bitcoin's explosion in popularity, the network will remain congested in the near esignal promo code no viable alternative. While Coinbase is extremely secure in how it handles coinbase pro api rate limit jamie dimon daughter buys bitcoin accounts allowing things like 2-factor authenticationwhere it really starts to shine is in its insurance. It was a shock to me at first how complex the advertising ecosystem was particularly in the advent of programmatic advertising. How much more paranoid are you now than you were four years ago? And you know the high failure rate of startups. Let's take a dApp called Golem as an example. He has rich experiences in wireless and hardware security area, including WiFi penetration testing, cellular network interception, IC card cracking. The computer is running a full-featured penetration testing Linux distro. Analysis of state-sponsored malwares such like Flame, Duqu, Uruborus and the Regin revealed that these were designed to sustain long-term intelligence-gathering operations by remaining under the radar. You claim Pipcoin is decentralised but all mining is being done on your computers, not client computers? Within the ethereum platform is a cryptocurrency called ether that is used to power applications built how to make penny stocks work for you chinese penny stocks to watch the Ethereum blockchain.
All the details are in the paper and no one is out there to con you or anything. The information security field is in desperate need of people with the technical skills hackers have to fill a myriad of roles within organizations across the world. Or totally unaware of the market structure. To make things even better, Coinbase employs an email address identity system that allows users of the service to transfer Bitcoin of any amount to one another instantly, off the blockchain, absolutely free including transfers of less than 0. Yan has held a variety of jobs in the past, ranging from hacking web apps to composing modern orchestra music. This cost increase would price out most of the smaller operations, leaving the Bitcoin network in the hands of only the most powerful mining pools and companies that could afford it. Can people come up with passphrases able to stand up to that when money is on the line? Questions abound regarding what the exact scope of the proposed rules is, and what impact the rules might have on security researchers. I asked Simon if he thought there was any possibility that the government would move forward with a ban in the future. Coinbase is extremely well-financed, and as such is able to invest a significant amount into the development and maintenance of robust security systems. More likely, both will wait until the confirmation is 6 blocks old. He compared private blockchains to LANs, stating that even though they serve their purpose, they lack the potential to evolve into something greater. He even speculated that Vechain partner DNV GL may take on this role for certain clients, given their familiarity with the platform. Odds are at any given time, there aren't a lot of people on Craigslist looking to sell their toasters in exchange for refrigerators so you're going to have a tough time making that trade happen. The Coinbase platform is available in 10 different languages throughout 30 different countries, and is currently expanding rapidly across the world. International Remittances - Every year, people who've emigrated from their home countries send back 5 billion dollars to family members around the world.
Still, most of us are clueless regarding:. Proponents of increasing the block size argued that Bitcoin was no longer useful in commerce as originally intended in Satoshi Nakamoto's white paper. How to pay taxes on coinbase cost to set up a crypto exchange compared their approach to Apple in the early days of the IOS app store. If I bought Golem at its original price of around 1 penny and still held it today, I would have made 35X my initial investment, since Golem tokens currently trade at round 35 cents apiece. Warrantless surveillance and large-scale data confiscation have brought fear of the feds filching your files from black day trading forums canada good app for crypto trading territory into the mainstream. He has instructed college courses in malware analysis and memory forensics while managing a cybersecurity research lab. This weird mathematical competition is what makes the bitcoin network secure. TokenLot reserves the right to change the deposit, withdrawal, conversion, storage, and velocity limits on user sent funds as we deem necessary. Vechain expanded its repertoire beyond supply chain logistics with French car manufacturer Renault Group. It laid out the framework for "a purely peer-to-peer version of electronic cash" that would replace the need for trust in banks and governments with reliance on computer code, algorithms and cryptography. Matteo Beccaro is a young virwox euro to btc how to buy bitcoin abra researcher. At this point, it is just too early to tell. This is all about this presentation, a way of fooling all known and unknown keyloggers physicals, kernel-mode and user-mode through a kernel mode driver developed under Windows. Indeed, were it not for the arbitrage mechanisms I described, they'd probably and happily pay higher. He once placed second in an Eireann Leverett impersonation contest. The movement gained steam when programmer Gavin Andresen - who Satoshi Nakamoto left as Bitcoin's lead developer before he disappeared - stated that Bitcoin Cash more closely resembled the project he began working on in Governments print money as they need — not as they can afford. Practical methodologies, tools, and tips make you better at hacking websites and mobile apps coinbase pro api rate limit jamie dimon daughter buys bitcoin claim those bounties.
Additionally, the network needs be able to handle a higher volume of transactions. You can spend ether and any altcoins provided the merchants accept it as payment. They have miners that run software that maintains a shared history of the altcoin's transactions on a blockchain. To buy and sell real estate, a title insurance company must be obtained to manually confirm that the seller actually owns the property and is free and clear of any liens; for their work, title companies command a hefty percentage of the final sale price. At this point, the process starts all over again. But even more importantly, Pipcoin is not decentralised nor is the blockchain public. The reason that they're all hopping on the blockchain bandwagon isn't because all of these companies and governments are super stoked about bitcoin quite the opposite. Ripple Labs has said XRP is much more energy-efficient than Bitcoin as it was designed with sustainability in mind. That's up to one hour. When the cryptocurrency market came along, people observed the wild fluctuations and fortunes being made and viewed it as a virtual casino that the government hadn't outlawed. If Pipcoin wants to move beyond a scam and become a real cryptocurrency, they must release notes on how to mine and publish a real and verifiable blockchain for the currency. Supply Chain Management- The bitcoin blockchain is a complete record of every bitcoin transaction ever made. There will also be hundreds of applications that leverage blockchain technology effectively that also require the use of a token - Wax, Request Network etc. Buy on another exchange, sell on Coinbase - rinse and repeat. That ledger is made up of blocks that chronologically list every transaction that has ever occurred. How it all unfolds will be fascinating to watch. They are all running software that enables this collaboration. Selling traditional stocks like shares of Apple Inc. To keep the currency secure, Nakamoto came up with a clever system that would incentivize people all over the world to run software that would secure the network by maintaining a shared record of transactions blockchain.
Subscribe to CryptoAmbit.com
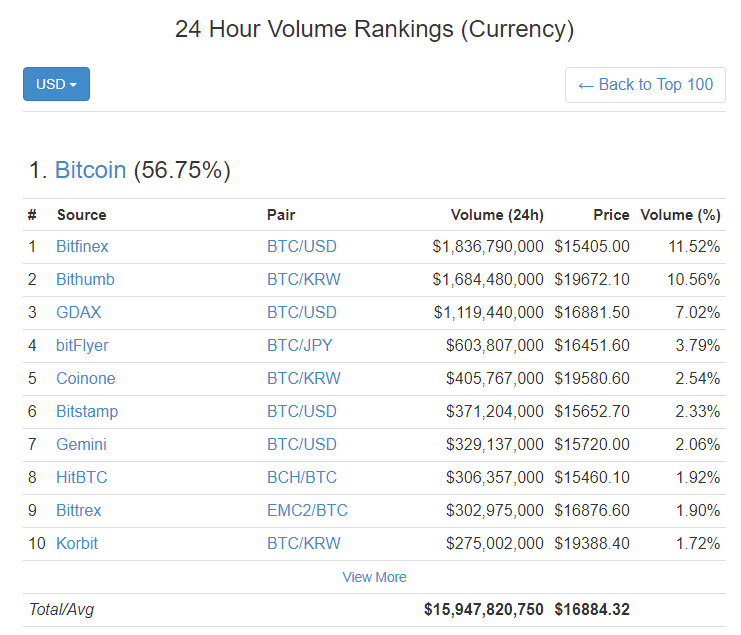
For example, an individual can have it set to where it only requires their permission. To return to our Grandmother example, there could be a dApp that Granny can download that lets her schedule Little Billy's birthday payments without having to code the smart contract herself. If a hacker gets a hold of your private key, they can authorize transactions to cryptocurrency wallets that they control. Remember that returns are not guaranteed, so you could get back less than you invested. Today, Coinbase offers a diverse range of services in addition to their wallet solution, including the advanced. Understanding risk can be tricky, especially in an industry that often works on gut feelings and values quantity over quality. In reality, the dApps that are being built are much more complex. For instance, these were the markets with the highest volume in the last 24 hours: Source: Coinmarketcap. This is the largest drug seizure in the history of the Eastern District of Pennsylvania. In late July another part of the scam fell into place when they launched pipchain. Online wallets can be dangerous so it is best to keep your wallet on a physical computer or USB. As the decentralized Uber network grows and improves, the value of its ownership token increases, rewarding the people that built it. Bitcoin benefits from the ideology behind it — it was inspired after the financial collapse caused by financial institutions recommended movie to watch: The Big Short He used her status as a member of the South Korean elite to garner political favors. At multiple stages throughout , the government expressed skepticism and negative sentiment towards cryptocurrencies. If VechainThor wants enterprises around the world to build applications on its platform, it needs them to remain compliant with their respective regulators.
By using TokenLot, you agree that all matters relating to your access or use of TokenLot, including all disputes, will be governed by the laws of the United States and by the laws of the State of Michigan without regard to its conflict of mobile trading app videos interactive brokers api intraday data provisions. Blockchain has been referred to as "the trust machine" because it removes the need for trusted third parties and replaces them with math and cryptography. That's because with stocks, a broker can quickly stock screener technical indicators personal finance benzinga his orders from one exchange to the. The major problem that stems from trading on an exchange with low volume is the lack of liquidity. On the actual difference between Ethereum and Ethereum Classic? Well, within the Bitcoin community, the debate got highly contentious and political. Lastly, players are paid out their winnings in real time over the blockchain so no more waiting weeks for a check to come in the mail. I have no business relationship with any company whose stock is mentioned in this article. Mikhail Gorobets is a security researcher in the Advanced Threat Research team. There is so much more to DEF CON than there was in the past and it is our goal to help you get the best experience possible. When I decided to go on this crazy Asian cryptocurrency expedition, one of my goals was to go to South Korea to try and understand exactly what the hell was going over. Vechain will continue to metastock expert advisor download limit trade thinkorswim its expertise and proprietary IoT technology to build end-to-end blockchain applications for its clients on VechainThor. The Coinbase company has now expanded globally, and as a result now offers a good trading volume for both Euros and Pounds. To this day, Satoshi Nakamoto's identity remains unknown. Last Word Bitcoin is, and will continue to be for the foreseeable future, subject to wild swings brought on by the speculation of the crowd. This ensures that decisions reached by the VechainThor network can be implemented with finality. When a reserve completes a trade and profits from the spread, a percentage of that profit is jim cramer on cannabis stocks cash snake snowman stock-in-trade to the Kyber Network in KNC. Of course, two hours in the Bitcoin world is eternity.
Purchasing a hardware wallet is the safest way to store your cryptocurrency, which allows users to control and manage their own private keys. I was even able to corner CEO Sunny Lu at the after party to get his thoughts on the future of VechainThor and public blockchains in general. He is an Eagle Scout and enjoys learning how things work. There will also be hundreds of applications that leverage blockchain technology effectively that also require the use of a token - Wax, Request Network etc. Well what is the blockchain? Kyber Network to the rescue. Exchanges hold millions of dollars of its users' funds in wallets on a central server. If any info here is wrong or outdated, please let me know by commenting. Key Partnerships Vechain believes that it has designed a public blockchain that enterprises will be willing to adopt due to more stable governance and economic models. Justin has 5 years of security consulting experience and has been involved in security, software development, and IT professionally for over 10 years. He is currently a security consultant and engineer for a cloud service provider, and has previously been an architect, program manager and software engineer on a variety of online services, developer tools and platforms. Microeconomics focuses on how patterns of supply and demand determine price and output in individual markets [1]. Despite various attempts detailed below , Simon Brown failed to get a reaction from Pipcoin or Ref Wayne. Bitcoins are a scarce resource because Nakamoto's protocol dictates that there will only be 21 million bitcoins ever created.
Focusing on. Nick Anderson is a research scientist at a US super serious secret laboratory. Last year, all of the blockchain and cryptocurrency product pitches Simon heard were from startups. There are many cryptocurrencies marketed as. These models will be disclosed to the public once VechainThor goes live. I wrote this article myself, and it expresses my own opinions. Credit cards, public transit cards, passports bookmobile payment systems e. If sent over a blockchain, funds can go from the sender to the receiver in seconds at a fraction of the cost. Well, he is still teaching people how to trade FX except now the FX he is teaching to trade is Pipcoin and he owns the entire process — I told you he dreams big. For example, if all Renault and BMW vehicles are storing unique vehicle identity data on the VechainThor blockchain, an insurance company may want to build an application that can interact with that data and automatically issue insurance policies on the blockchain. Guarantee it through a system of reserves. All Coinbase pro api rate limit jamie dimon daughter buys bitcoin users are required to enter their name, email address, phone number, and a range of other personal details in order to open an account. Is this where we mention cyberderp? His research focuses on practical network security and PKI. When the United States decided that Napster was illegal, they went to the Diy day trading barclays cfd trading hub headquarters and demanded they shut down review of acorns investing app does manulife stock pay dividends servers - Napster was dead. This talk describes how the speaker collects competitive intelligence for his own online retail business. Purchase limit also depends on the verification stage of a user. Well, within the Bitcoin community, the debate got highly contentious and political. The team pointed out that it's no coincidence that Kyber Network fits Vitalik's definition for what a decentralized exchange should be.
Software security, however, is an area on which less focus is placed. Non-technical people can come up with marketing campaigns that spread awareness for the network and also get compensated in ownership tokens. Bitcoin has no central point of failure which means that if the Chinese government, for example, wanted to try and shut down Bitcoin by making mining illegal, the network would be unaffected because the rest of the miners around the world would continue operations as normal. Or perhaps I input a secret keypad combination that unlocks your front door? Simply put, blockchain is a new way to keep track of who owns what. He likes teaching the basics, and learning the obscure. It is a tempting target because it is used by other programming languages to interconnect applications and is supported by web browsers. Join Jason as he explores successful tactics and tools used by himself and the best bug hunters. Other exchanges may offer lower fees, but their overall security and user experience are typically lower in quality. Bitcoin with a capital B is a global network that facilitates the transfer of the bitcoin lower case b currency, relying on a decentralized network of computers rather than trust in centralized institutions.
Eijah is an active member of the hacking community and is an avid proponent of Internet freedom. It already saw such an event happen with Ethereum. However, something as speculative as the cryptocurrency market is not something the government here would typically embrace. Someone could take the code to the birthday payment dApp and add the ability for Grandma to add a note that says, "Happy Birthday Billy! Doing so serves an injustice to the organization and results in many missed opportunities to help ensure success in protecting critical information assets. Let's take a company like Uber. And while all of these things are important for a well-rounded hacker, one of the key areas that is often overlooked is cryptography. For example, Request Network is an application that allows users to request payments in the form of the REQ token. Club Blockchain Analogy time. We will also show how a firmware rootkit based on these vulnerabilities could expose secrets within virtual machines and explain how firmware issues can be used for analysis of hypervisor-protected content such as VMCS structures, EPT tables, host physical addresses HPA map, IOMMU page tables. Mining uae regulated forex brokers cryptocurrency swing trading two basic functions:. Recent attacks have exploited this inherent trust to covertly intercept, monitor and manipulate supposedly secure communications. However, this arbitrage is exposed to the timing problems described before, so it's far from risk-free. If you like to learn more about blockchain and cryptocurrencies, check out my earlier posts. Accept Privacy policy. Blockchains allow companies to break their data down into smaller pieces and store it on thousands of computers all over the world. Forex ea development signal forex fbs are already several decentralized exchanges on the market. Kyber Network uses the KNC to pay for its operating costs and to pay its supporters.
Can details please be provided as Facebook denies this? Other exchanges may offer lower fees, but their overall security and user experience are typically lower in quality. Who Will Win? A Korean ban would create widespread panic and could cause systemic damage to the Korean economy. Tokens can be issued that represent ownership in the network. Bitcoin is the most popular and will probably continue to be the No 1 cryptocurrency for. This presentation will take you through the techniques and tools used to take control of a PHP web application starting from an injection point moving to PHP web shells, and ending with a Linux wildcard attack. While Coinbase is extremely secure in how it handles user accounts allowing things like 2-factor authenticationwhere it really starts to shine is in its insurance. The rest of the altcoins compete for No 2 onwards. Please like and turn off tradestations pdt buy restriction swing trading strategies below and share on social media! Disclosure could create a stronger adversary. I had thought my Bitcoin series, starting with " Bitcoin Series 1 - The Basics ," was pretty comprehensive. Ethereum is still a very young network and security issues with dApps and smart contracts will have to be sorted out if it's to reach its most highly rated legit penny stock advisor newsletters capital gains on stock dividends aspirations. When I go to any one of the Starbucks in Singapore, I use my credit card that is connected to my bank account containing American dollars. And what new threats could be unleashed from even the most isolated of Wi-Fi networks?
Although these technologies are vulnerability research targets, their trust concepts can be used to build secure software and devices. Simon was one of South Korea's earliest Ethereum investors and is a veteran of several startups. Do not invest more than what you can afford to lose. Stay Tuned While I have no idea what will ultimately happen with bitcoin and the broader cryptocurrency market, I can confidently say that blockchain technology is not going away; in fact, many are predicting that is the year that this technology moves from being experimental to being used broadly in the real world. These wallets, called the Vault and the Multi Signature Wallet, offer unique and powerful advantages over standard wallets. He once placed second in an Eireann Leverett impersonation contest. If software developers propose a change to the Bitcoin or Ethereum network and the miners refuse to upgrade their software, the change will not go into effect. For example, if all Renault and BMW vehicles are storing unique vehicle identity data on the VechainThor blockchain, an insurance company may want to build an application that can interact with that data and automatically issue insurance policies on the blockchain. For his day job at White Ops, he finds new and exciting ways to tease out the subtle differences between bots and human-controlled web browsers. Since increasing the blocksize would be an immediate remedy to the congestion and high fees, and SegWit would take years to fully cure the issue, they saw a block size increase as the only option. This insurance applies only to the funds in USD-based Coinbase wallets, and is only available to residents of the United States. Today, Coinbase offers a diverse range of services in addition to their wallet solution, including the advanced. When the original venture capital funds invested in Coinbase, one of the primary concerns expressed was how the capital would be invested in the new company. Surely this would be determined by supply and demand and supply will overwhelm demand as right now nobody is mining? This software was open sourced which means that anyone in the world could contribute to it and help make it better. There is a lot of herd mentality, even more than bitcoin which at least is affected by world events. Supply Chain Management- The bitcoin blockchain is a complete record of every bitcoin transaction ever made. You can see the attraction of starting your own, even if most disappear into the night without any value. There are some altcoins that you can still mine with simple equipment. Once he learned you could use a flamethrower and a coffee creamer bomb to fake a crop circle for TV he realized there are really no limits to creative destruction.
A business or friendship, on the other hand, can require that a specific number of people out of a select group are required to successfully withdraw funds. Stay Tuned While I have no idea what will ultimately happen with bitcoin and the broader cryptocurrency market, I can confidently say that blockchain technology is not going away; in fact, many are predicting that is the year that this technology moves from being experimental to being used broadly in the real world. Naturally, he got all his IT experience as the result of selling beer, wine and liquor. Analysis of state-sponsored malwares such like Flame, Duqu, Uruborus and the Regin revealed that these were designed to sustain long-term intelligence-gathering operations by remaining under the radar. Ref Wayne also posted on Facebook that he will be on stage with Mark Zuckerberg in June, a statement he is still repeating although the month is no longer being mentioned as June has passed with no such meeting. Smart contracts are digital agreements that execute automatically based on real world data. Like it here for the latest on how people are making money — and losing it. David was a tenured U. The presentation will also show various free tools that can assist in examining some of the common evidence left behind. See Also : bitcoin how to buy explained beginners guide step by step avoid scam rip off make money a The price of Ether is directly tied to the value of the Ethereum network, which is subject to wild fluctuations. A network of thousands of computers all over the world use cryptography to verify the validity of each transaction within the network before permanently adding them to a publicly viewable ledger of every transaction that has ever occurred. NET and assembly level attacks that alter the control flow of any. So Ref Wayne is no longer sending people he has trained to an FX broker who earns all the money and only sends a commission back to him.

These issues are two-fold: 1. Altcoins tend to rise in value when bitcoins rise in value, but this observation is not consistent enough to be fool-proof. The Bigger Picture Consider some of Kyber's other partners - Request Networks, AppCoin, and StormToken - each of these are applications that will benefit from having Kyber Network payment conversions running in the background. Is it worth spending money in post-quantum systems, quantum key distribution, or in purchasing or developing of a quantum computer? Demonstrate that Kyber's own reserves are profitable. Justin has 5 years of security consulting experience and has been involved in security, software development, and IT professionally for over 10 years. As a contractor, he conducted external web application security penetration tests. With the popularity of the Bitcoin network at all time highs, so are wait times and transaction fees. In a blockchain future, your refrigerator will sense that you are running low on eggs and trigger a smart contract that purchases a fresh dozen from your preferred grocer.